
Swiping for Clues: A Fun Beginner’s Guide to Mobile Forensics 📲
Dive into the wild world of mobile forensics—learn how investigators extract and analyze smartphone data, catch cybercriminals, and outsmart burner phones like a digital detective.
TL;DR 🧠
Mobile forensics = digging through phones to find deleted texts, location trails, and sketchy screenshots. Think: unlocking a suspect's digital diary with tools like Cellebrite and Magnet AXIOM. 🔓📲
What is Mobile Forensics Anyway?
Mobile forensics is the science of recovering digital evidence from mobile devices, including:
Smartphones and tablets (Android, iOS, even the odd Windows Phone—RIP)
SIM cards and SD cards
Messaging apps, call logs, photos, GPS data, and more
Unlike computer forensics, where files sit politely in directories, mobile data is messy, fragmented, and encrypted tighter than your Netflix password.
“Today’s criminals don’t carry briefcases—they carry burner phones.”
📚 — Lee Reiber, Author of “Mobile Forensic Investigations”
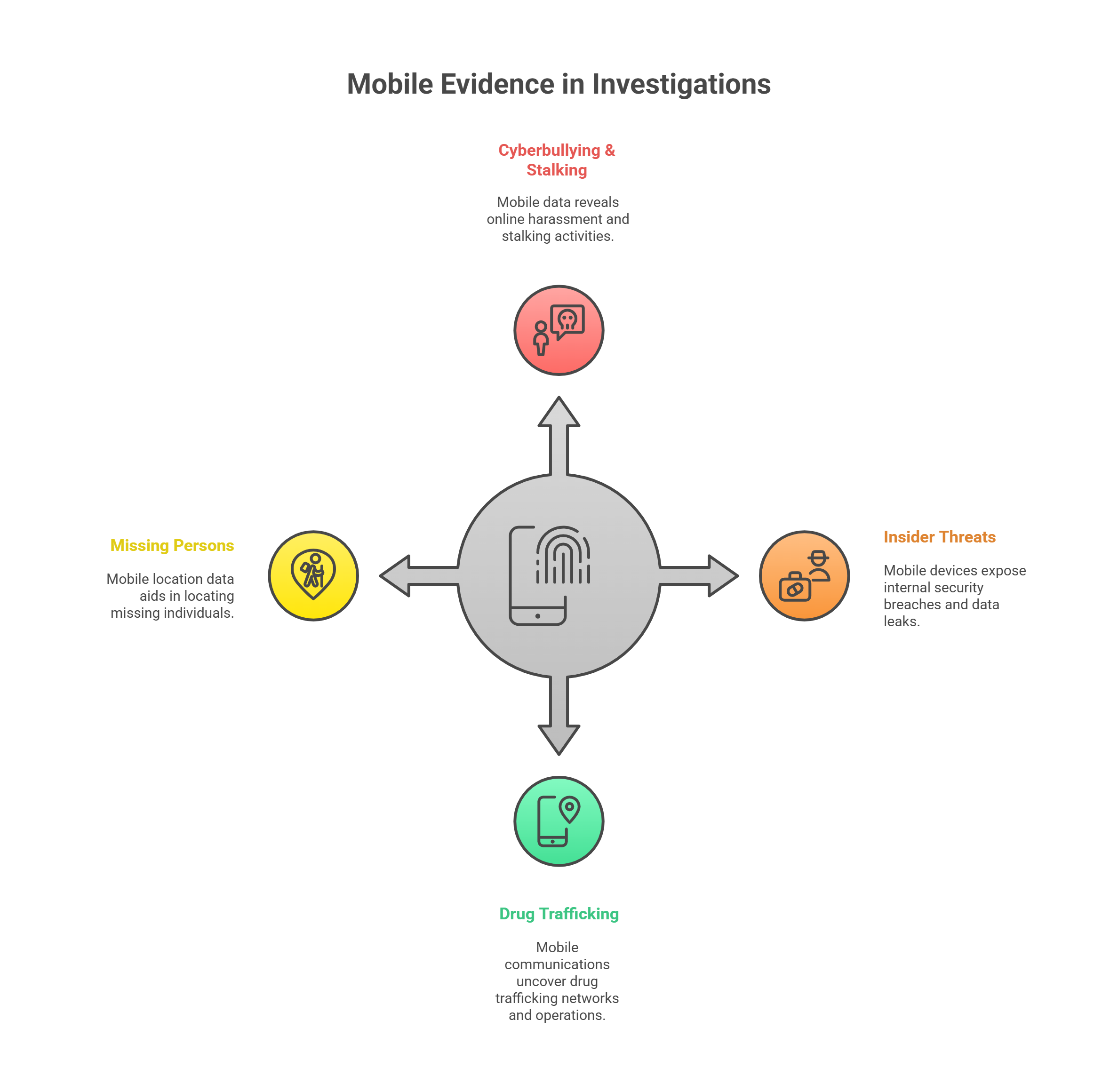
Why It Matters 📱💣
With 90%+ of the world using mobile phones for communication, most modern investigations involve mobile evidence. That includes:
Cyberbullying & stalking cases
Insider threats at companies
Drug trafficking operations
Location tracking in missing persons cases
Whether it’s an iMessage or a shady APK install, phones tell stories computers can’t.
Phases of a Mobile Forensics Investigation 🔍
1. Seizure & Preservation
Lock the device down—literally. Use Faraday bags or Airplane Mode to prevent remote wiping. The goal? Preserve the scene before the suspect tries a digital Houdini.
2. Acquisition
This is where the magic (and frustration) happens.
Method |
Description |
Risk Level |
|---|---|---|
Logical |
Pulls active files (easy, limited) |
🔓 Low |
File System |
Grabs deeper directories, app data |
⚠️ Medium |
Physical |
Bit-by-bit image (includes deleted data) |
🔒 High |
Chip-off |
Direct NAND chip read (last resort) |
💣 Expert |
Popular tools? Cellebrite UFED, Magnet AXIOM, Oxygen Forensics, and MSAB XRY. Each one is basically Inspector Gadget with a USB cable.
3. Analysis
This is where you dig through:
Call and SMS logs (green bubbles leave clues too 👀)
App data: WhatsApp, Signal, Telegram, TikTok, etc.
Photos & videos: Metadata can reveal time, GPS, even device model
Browser history: No, “Incognito” doesn't mean invisible
4. Reporting
Wrap up your findings in a forensically sound report. Include timelines, hashes, extraction methods, and all juicy data—minus your caffeine breakdowns.
iOS vs Android: The Digital Cage Match ⚔️
Feature |
Android |
iOS |
|---|---|---|
🔐 Encryption |
Varies by device/version |
Strong, full-device by default |
🔧 File Access |
More flexible, especially rooted |
Locked down like Fort Knox |
🧰 Forensic Tools |
Cellebrite, Magnet, Oxygen, XRY |
Mostly Cellebrite & GrayKey |
💀 Deleted Data |
Easier to recover (unless wiped) |
Often overwritten quickly |
Pro Tip: iOS 16+ is making extractions harder by limiting USB debugging—even more reason to stay sharp and up-to-date on tools.
Common Mobile Forensics Challenges 😬
Encryption everywhere (Apple really said: “not today, FBI”)
App sandboxing prevents easy access
Cloud syncing makes evidence appear off-device
Fast-paced updates outpace forensic tool support
Real-World Scenario: Infamous Phishing Ring Busted
Authorities traced stolen credentials to a WhatsApp group organizing attacks. Using a seized Android device, investigators extracted:
Group chats coordinating the campaign
GPS history of drop locations
Browser bookmarks linking to phishing kits
Voice messages with recruitment pitches
Takeaway? Sometimes the villain keeps receipts... in voice memo form.
TL;DR Recap 🎯
Mobile forensics digs into devices for calls, texts, GPS, app logs, deleted files
Logical, file system, physical, and chip-off are key acquisition types
Tools like Cellebrite, Magnet AXIOM, and Oxygen Forensics are top-tier
iOS and Android each have their own extraction nightmares
Great for law enforcement, cybersecurity teams, and certified pros
Craving More Mobile Mojo? 📲
That’s just the surface, detective. Want to unlock deeper digital crime-fighting knowledge? Stick with our blog for upcoming breakdowns on so much more!
Tags: Mobile Forensics, iOS Forensics, Android Forensics, Smartphone Data Recovery, Digital Forensics, Cellebrite, Mobile Security, Forensic Tools
 Add Row
Add Row  Add
Add 




Write A Comment