
Malware Forensics: How to Dissect the Monsters Lurking in Your Machine 💀
Dive into the world of malware forensics: uncover types of malware, their behavior, and how forensics experts analyze malicious code using static and dynamic techniques. 🧬⚙️
This is the final article of our EC-Council Digital Forensics Essentials (DFE) series.
TL;DR 🎯
Malware forensics is the art of figuring out what hit your system, how, and why it’s currently asking for $10,000 in Bitcoin. We’re talking trojans, rootkits, ransomware, and how to analyze them without accidentally turning your lab into a hacker’s vacation home. 🏖️🔓
What Is Malware Forensics?
Malware forensics is the investigation of malicious software behavior, origin, and impact on systems and networks. Think of it like an autopsy... except the corpse is your infected laptop, and the killer might be a sneaky Excel spreadsheet with a macro addiction.
🧟♂️ Meet the Malware: Types, Components & Delivery Tricks
Common Malware Types:
Malware Type |
What It Does |
|---|---|
Virus |
Self-replicates and infects files |
Worm |
Spreads across systems without user input |
Trojan Horse |
Disguised as legit software (thanks a lot, "FreeGameSetup(dot)exe") |
Ransomware |
Encrypts files, demands ransom |
Rootkit |
Hides itself at the OS/kernel level |
Spyware |
Tracks user activity, often for data theft |
Adware |
Shows unwanted ads—annoying, but still a crime when bundled with spyware |
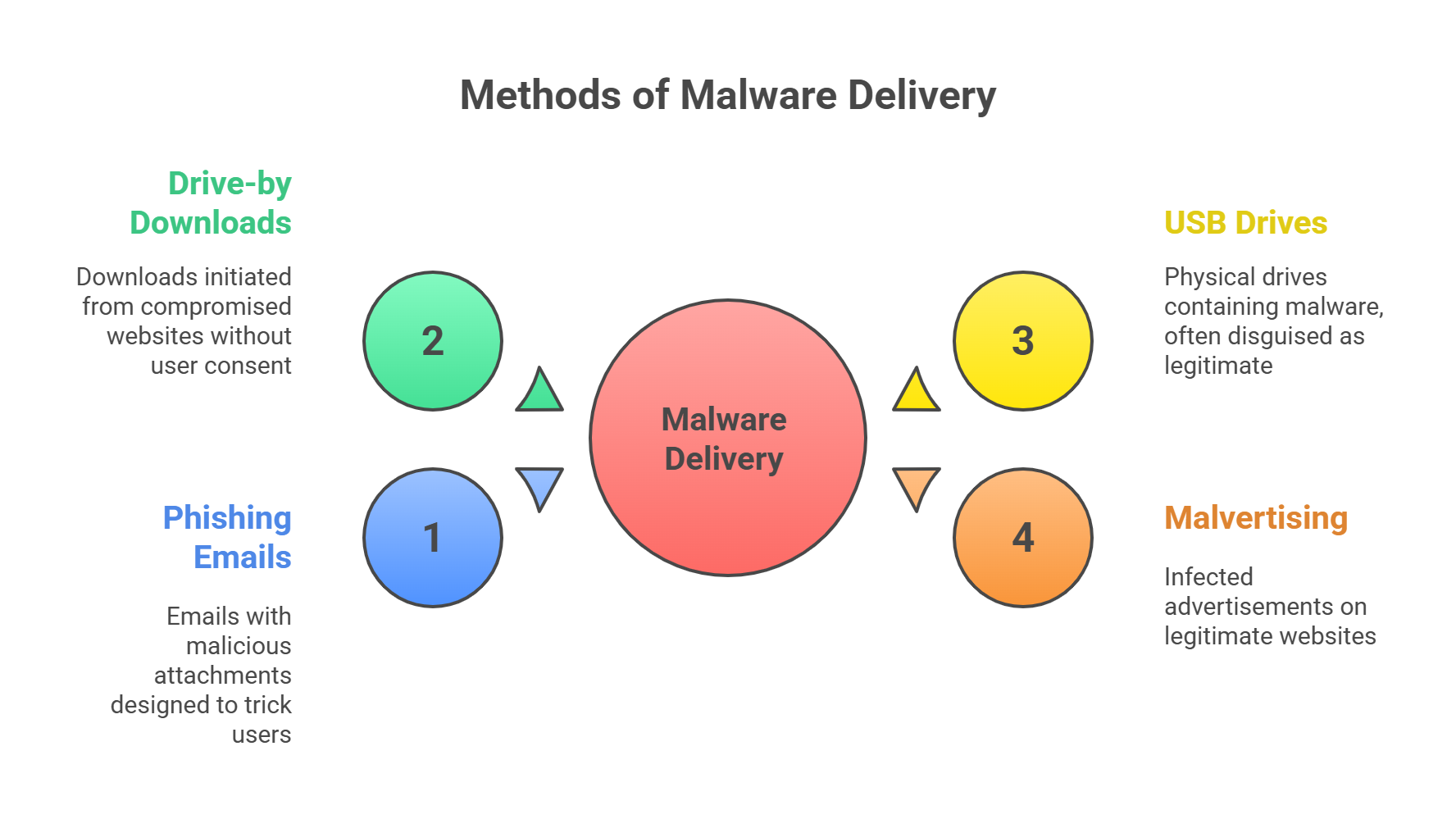
Delivery Methods:
Phishing emails with weaponized attachments
Drive-by downloads from compromised sites
USB drives (aka “digital landmines”)
Malvertising (infected ads on legit websites)
🛠️ Malware Forensics: Static vs. Dynamic Analysis
Forensic analysts have two main flavors of malware analysis. One is safer. The other is riskier. Both are essential.
🔍 Static Analysis (Look, Don’t Touch)
No execution required
-
Involves checking:
File hashes
Strings (using tools like
stringsorBinText)Embedded resources
File headers (EXE, DLL, PDF, etc.)
Use VirusTotal, PEStudio, IDA Pro, or Ghidra for deep dives
💡 Why it matters: It’s safer than bringing malware to life. Think "reading the recipe" without baking the cake that might explode.
⚙️ Dynamic Analysis (Touch Carefully)
Involves executing malware in a sandbox environment
-
Monitors:
Network traffic (Who’s it calling? What’s it stealing?)
File system changes
Registry modifications
API calls and process activity
Tools include: Cuckoo Sandbox, Any.Run, Process Monitor, and Wireshark
💡 Why it matters: You see the real behavior—but only if you don't mind risking a virtual “oh crap” moment.
📄 Analyzing Suspicious Documents (AKA: When Word Docs Go Rogue)
Malware loves a good disguise. That invoice from "CEO Karen"? Yeah... probably packing macros.
Common File-Based Threats:
Macro malware in Office docs
Embedded JavaScript in PDFs
HTML attachments that load malicious scripts
Obfuscated scripts (Base64, ROT13, XOR—you name it)
Use tools like:
OLETools for extracting macros
PDF Examiner or PDF-Parser
Hybrid Analysis to see the document’s behavior in the wild
🔎 System and Network Behavior Analysis
A smart analyst doesn’t just look at the malware—they watch the scene of the crime too.
System Behavior Forensics:
Monitor CPU/RAM usage spikes
Watch which files/folders were created or altered
Investigate registry changes (classic malware tactic)
Network Behavior Forensics:
Check for Command and Control (C2) callbacks
Analyze packet captures with Wireshark or tcpdump
Identify domains or IPs using threat intel sources
🔐 “Malware without a network is like a thief without a getaway car.”
— Lenny Zeltser, Malware Reverse Engineering Instructor, SANS Institute
[Source: SANS Malware Analysis Poster]
TL;DR Wrap-Up 🎓
Malware comes in all shapes: viruses, worms, ransomware, and more.
It’s delivered via phishing, sketchy downloads, and sometimes inside PDFs.
Static analysis = safe scanning. Dynamic = risky business in a sandbox.
Forensic investigation includes file inspection, system monitoring, and network analysis.
Tools of the trade? VirusTotal, IDA Pro, Cuckoo Sandbox, Wireshark, and some serious nerves of steel.
🎉 You Made It! Now You’re DFE-Certified Savage Material
This wraps up our epic blog series on the EC-Council Digital Forensics Essentials (DFE) certification.
📚 Want to keep sharpening your skills? Check out more deep-dives on:
CEH (Certified Ethical Hacker)
👉 Bookmark this blog, follow us for more, and remember—every file has a story. Have a friend who'd appreciate this? Pass it along! 🔍🖥️
Tags: Malware Forensics, Digital Forensics, Static Analysis, Dynamic Analysis, Cybersecurity, EC-Council DFE, Malware Types, System Behavior, Suspicious Documents
 Add Row
Add Row  Add
Add 




Write A Comment