
Hack the Hackers: How to Outsmart Anti-Forensics Tactics Like a Digital Ninja 🧠
Learn to identify and counter anti-forensics techniques in this EC-Council Digital Forensics Essentials module. Outsmart hackers and protect digital evidence with pro-level forensic tactics.
TL;DR 🕶️
Anti-forensics is the hacker’s way of erasing their footprints, setting traps, and flipping the script on forensic investigators. Your job? Recognize these sneaky tactics and bring digital justice—clean, clear, and courtroom-ready. 🧑⚖️💻
What is Anti-Forensics? (Besides Being Really Annoying)
Anti-forensics = anything that interferes with the collection, preservation, or analysis of digital evidence.
It’s basically the hacker’s version of:
“I didn’t do it.”
“You can’t prove it.”
“Oops, did I just encrypt that file and delete the original?”
Common Anti-Forensics Goals:
Delay investigation
Destroy or alter evidence
Deceive investigators
Dodge legal consequences
As forensic expert Cory Altheide notes:
“The goal of anti-forensics is not just destruction—it’s manipulation. They want you to chase ghosts.”
📚 “Digital Forensics with Open Source Tools,” Altheide & Carvey, 2011
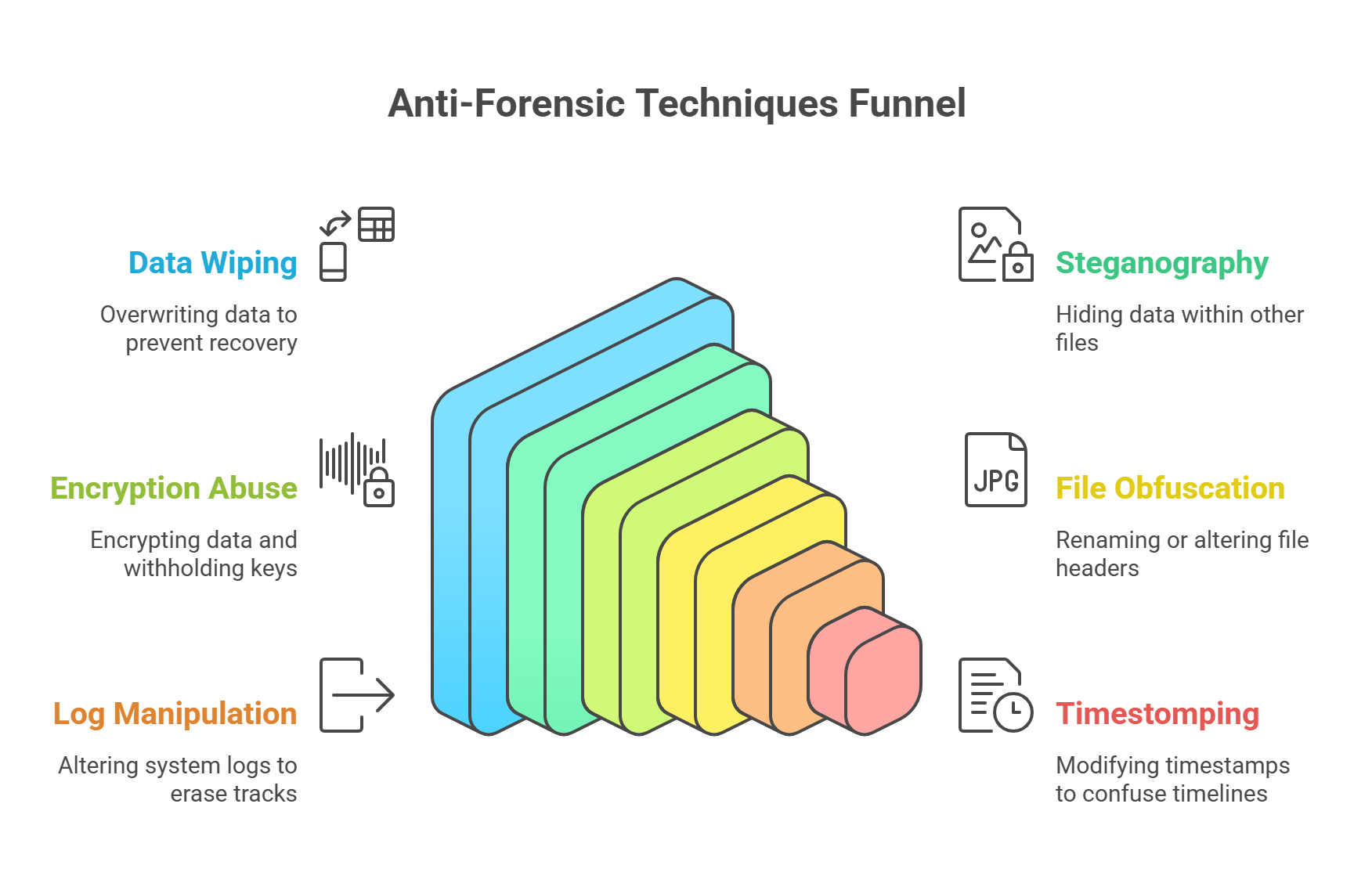
Anti-Forensics Techniques (aka Hacker Shenanigans)
Here’s how the digital crooks mess with the evidence—so you can stop them cold:
🧽 1. Data Wiping and Secure Deletion
Tools like CCleaner, BleachBit, or sdelete overwrite data multiple times.
Makes traditional file recovery tools useless.
🧪 2. Steganography
Hides data inside other files, like images or audio.
Think of it as digital smuggling—hiding contraband in grandma’s cookie jar.
🔒 3. Encryption Abuse
Encrypt everything, then refuse to provide the key.
You might find the data, but good luck reading it.
🧮 4. File Obfuscation and Renaming
Renaming
.exeto.jpgor changing file headers.It’s like a criminal wearing a name tag that says “Not the Criminal.”
🧱 5. Log File Manipulation
Altering system logs to erase tracks or create fake ones.
Now you’re not just missing the smoking gun—the gun never existed.
👻 6. Timestomping
Modifying timestamps to confuse the timeline of events.
“No officer, that malware was installed before I got the laptop.”
How Forensic Investigators Fight Back (Cue Hero Music 🎶)
You don’t need a cape, just a killer toolkit and a sharp mind.
🛡️ 1. Use Verified Imaging Tools
Tools like FTK Imager, dd, or EnCase ensure bit-level duplication and help detect missing sectors, modified headers, and metadata inconsistencies.
🐍 2. Hash Everything
By comparing hashes of original and imaged data, you’ll know if something smells phishy 🐟.
🔬 3. Metadata Analysis
Even if a file’s been renamed or modified, metadata often spills the tea:
Creation timestamps
User accounts
Last accessed info
🕵️ 4. Carve Hidden Files
Use tools like Scalpel, Foremost, or Autopsy to recover deleted files or inspect slack space.
Because sometimes the truth is hiding in the digital couch cushions.
🔦 5. Detect Steganography
Use forensic stego scanners like Stegdetect to find data hiding in plain sight.
⚖️ 6. Maintain Chain of Custody
Solid documentation helps prove tampering and protect evidence from claims of mishandling.
Example: The Crypto-Crook Who Got Caught
A 2022 case study by EC-Council training instructor Eric Reid showed how a criminal used TrueCrypt to encrypt evidence—but forgot that the bootloader (unprotected) revealed enough of the file structure to prove intent.
📚 EC-Council Casebook Series: Volume 4 – “When Encryption Fails”

Real Talk: This Stuff is Hard… but So Are You 💪
The bad guys will try to outsmart you. But you’ve got:
The tools.
The techniques.
The tenacity.
And maybe a really strong coffee habit. ☕😅
TL;DR Recap: How to Defeat the Data-Ninjas
Anti-forensics = digital sabotage.
Common tricks: wiping, stego, timestamps, encryption.
Fight back with verified tools, metadata analysis, and bit-level imaging.
Hash everything. Seriously. Hash it like your digital life depends on it.
Still Thirsty for Digital Justice?
Keep riding the byte wave with our upcoming articles, where we unpack file systems like pros and show you how to pull evidence from even the most stubborn storage.
Tags: Anti-Forensics, Digital Forensics, Cybercrime, EC-Council DFE, Evidence Tampering, Forensic Countermeasures, Data Obfuscation
 Add Row
Add Row  Add
Add 




Write A Comment