
“CSI: Ctrl+Alt+Delete” – Mastering the Digital Forensics Essentials (EC-Council DFE) 🔎
Break into digital forensics with this fun, expert guide to EC-Council’s DFE Computer Forensics Fundamentals module. Learn the essentials with real-world insights.
TL;DR 🧠
Computer forensics isn’t just for hoodie-wearing hackers on TV. It’s about collecting, preserving, and analyzing digital evidence (without accidentally nuking it). This article covers the EC-Council Digital Forensics Essentials certification's first module—Computer Forensics Fundamentals—in a way that won’t make your eyes glaze over like a glazed donut on a Monday morning. 🍩 Let’s get you one step closer to becoming the digital detective you were born to be.
What Is Computer Forensics… and Why Should You Care? 💾
Imagine your laptop is a crime scene. (RIP personal space.) Now imagine someone actually knows how to find deleted files, trace IP addresses, and explain your browser history in court. That’s a computer forensic investigator.
According to Chuck Easttom, author of Computer Security Fundamentals and a Certified Forensics Examiner, “Computer forensics is the art and science of extracting data from digital devices in a way that’s accurate, legal, and repeatable.” (Easttom, 2022)
In short: if data is the new gold, then forensic investigators are the digital prospectors—with fancier coffee.
🔍 Understanding Digital Evidence: It's Not All Ones and Zeros
Digital evidence is any data that can prove something happened on a device. It could be:
A deleted email 💌
Browser history (uh-oh)
Chat logs, IP logs, file timestamps
But not all evidence is created equal. Here’s the breakdown:
Type of Evidence |
What It Means |
|---|---|
Real Evidence |
Hard drives, USBs, etc. You can touch it. |
Documentary |
Digital records, screenshots, or logs. |
Demonstrative |
Visuals that help explain other evidence. |
Testimonial |
The classic: “He told me the password was ‘1234’.” |
Digital evidence must be admissible, authentic, complete, and reliable. So no, your cousin’s “totally real” screen recording of your Minecraft server meltdown probably won't hold up in court. 🎮
🛡️ Forensic Readiness: Be Prepared (Like a Cyber Boy Scout)
“Forensic readiness” means your systems are prepped to collect evidence before something shady goes down. It’s not just smart—it’s legally strategic.
A Forensically Ready System:
Logs activity (accurately)
Has data retention policies
Uses access controls
Can recover data after an incident
Dr. Bill Nelson, co-author of Guide to Computer Forensics and Investigations, calls forensic readiness “a crucial part of minimizing downtime and liability in a breach.” (Nelson et al., 2023)
Translation: Don’t wait for a breach to start acting smart.

🕵️♂️ What Forensic Investigators Actually Do (It’s Not All Cool Sunglasses and One-Liners) 😎
Sure, it looks glamorous in the movies. But real digital forensic work involves:
Collecting and preserving data
Analyzing digital trails (logs, metadata, file remnants)
Writing airtight reports (yes, you’ll be typing—a lot)
Testifying in court (or prepping someone who will)
They must be impartial, methodical, and obsessive about chain of custody—aka who touched what, when, and why. If evidence is mishandled? The case could collapse faster than your Wi-Fi during a Zoom meeting.
Legal Compliance in Computer Forensics: Don’t Be “That Guy” ⚖️
If you collect digital evidence without knowing the laws? Congrats, you’ve just gone from analyst to accidental criminal. 🫠
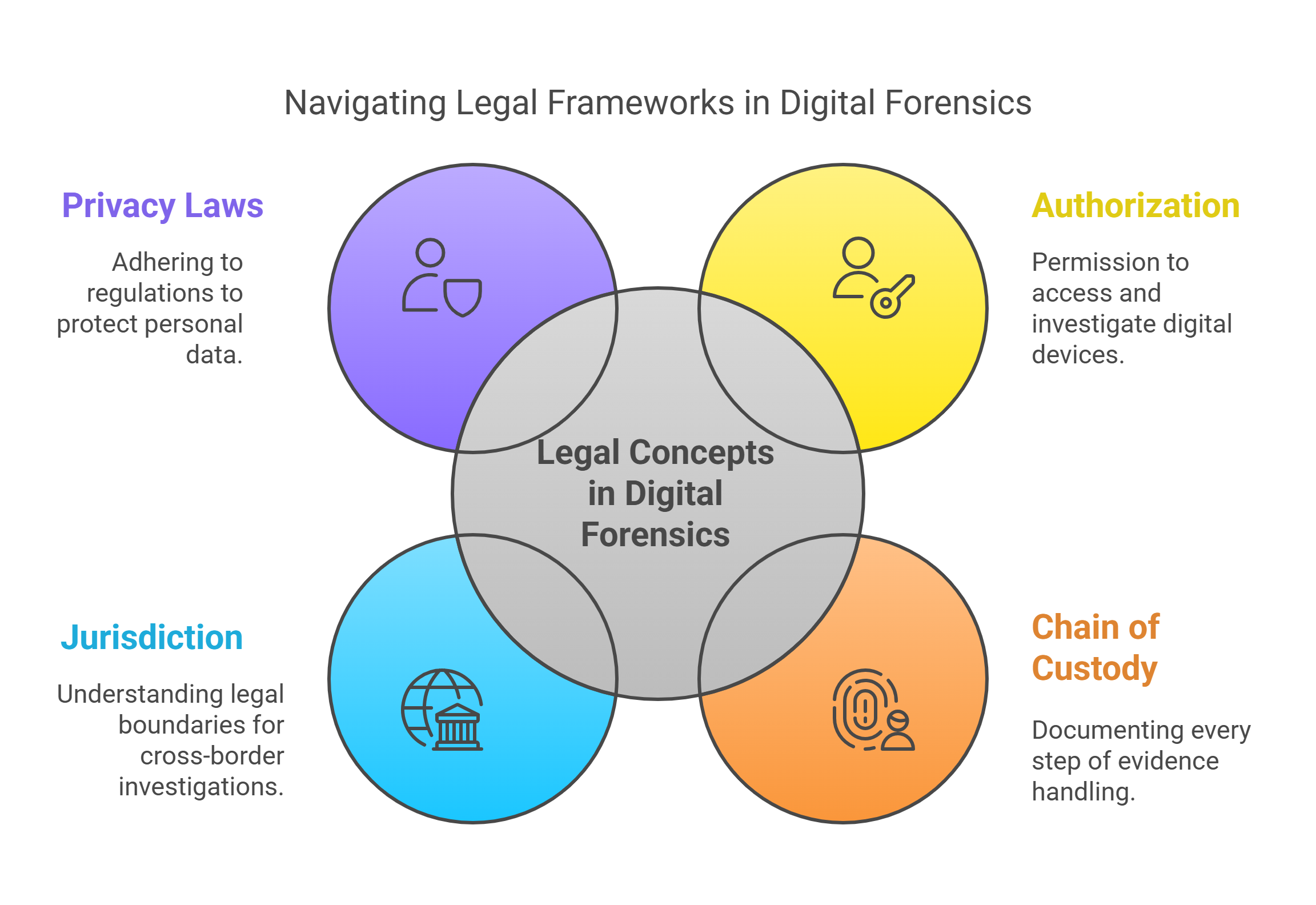
Key Legal Concepts:
Authorization: You can’t investigate what you don’t have permission to touch.
Chain of Custody: Document every step you take. Seriously. Every. Step.
Jurisdiction: If the device is in another country? Things just got complicated.
Privacy Laws: Data collection = surveillance. Know the rules (and the consequences).
As Mark Pollitt, former director of the FBI’s Computer Analysis Response Team, once said, “The law may not always keep up with technology, but it will always catch up to you.” (Pollitt, 2020)
So, Why Go After the EC-Council Digital Forensics Essentials Cert?
Because it’s your stepping stone to becoming the cyber-sleuth every company needs. It:
Builds a strong foundation in digital forensics
Gives you the lingo and legal literacy
Prepares you for deeper certs like CHFI (Certified Hacking Forensic Investigator)
Proves to employers you're not just “good with computers”—you’re certified dangerous (in a good way) 💼🔥
TL;DR (Again): The Bare-Bones Recap 🍖
Computer forensics = CSI for your hard drive.
Evidence comes in all digital shapes and sizes.
Forensic readiness makes a good offense the best defense.
Investigators are digital detectives with legal street smarts.
Without legal compliance? You're toast.
EC-Council DFE gives you everything you need to level up.
Ready to Keep Digging into Digital Forensics?
If this article got your curiosity buzzing louder than a hard drive from 2008, check out our other guides on certifications, ethical hacking, and building a career in cybersecurity.
🔗 Bookmark, and don’t forget to look for the next article: "Ctrl+F for Clues" - The Computer Forensics Investigation Process Decoded."
Tags: EC-Council, Digital Forensics, Cybersecurity Certification, Computer Forensics, Digital Evidence, Forensic Investigator, Gen Z IT Learning
 Add Row
Add Row  Add
Add 




Write A Comment