
Zero Trust in a Work-From-Anywhere World: Beyond the Buzzword
You've probably heard the term "Zero Trust" floating around like that catchy but slightly annoying song you can't get out of your head. It sounds super important and techy, right? Like something straight out of a spy movie where everyone's double-crossing everyone else (spoiler alert: in cybersecurity, they kinda are!). But what is it really, especially now that our "office" could be our kitchen table, a coffee shop in Bali, or even that weird corner of your attic you've finally claimed?
Fear not, future Microsoft SC-900 certified superheroes! We're here to demystify Zero Trust and show you it's not some mythical creature but a super practical approach to keeping your digital goodies safe in this wild, work-from-anywhere world. Think of this as your fun, no-nonsense crash course – no boring lectures, promise!
Ditching the "Trust Everyone Inside" Mentality: The Medieval Castle Analogy
Imagine the olden days (think knights and dragons, but with slightly less reliable Wi-Fi). Traditional network security was like a medieval castle. Once you were inside the castle walls, you were generally trusted. Knights, servants, even the occasional suspiciously shifty-looking jester – all good. The focus was on keeping the outsiders out with big walls and moats (firewalls and VPNs in our digital world).
But what happens if a sneaky bad guy (a threat actor) somehow gets inside those walls? Or worse, what if one of those "trusted" insiders turns out to be a double agent (insider threat)? Chaos ensues! The whole kingdom (your network) is vulnerable.
Zero Trust says, "Hold up! Let's ditch this 'trust everyone inside' nonsense." Instead, it operates on the principle of "never trust, always verify." Think of it as having super strict security checkpoints within the castle walls. Every knight, every servant, even the king himself has to show their ID and prove they have the right to access specific areas and resources.

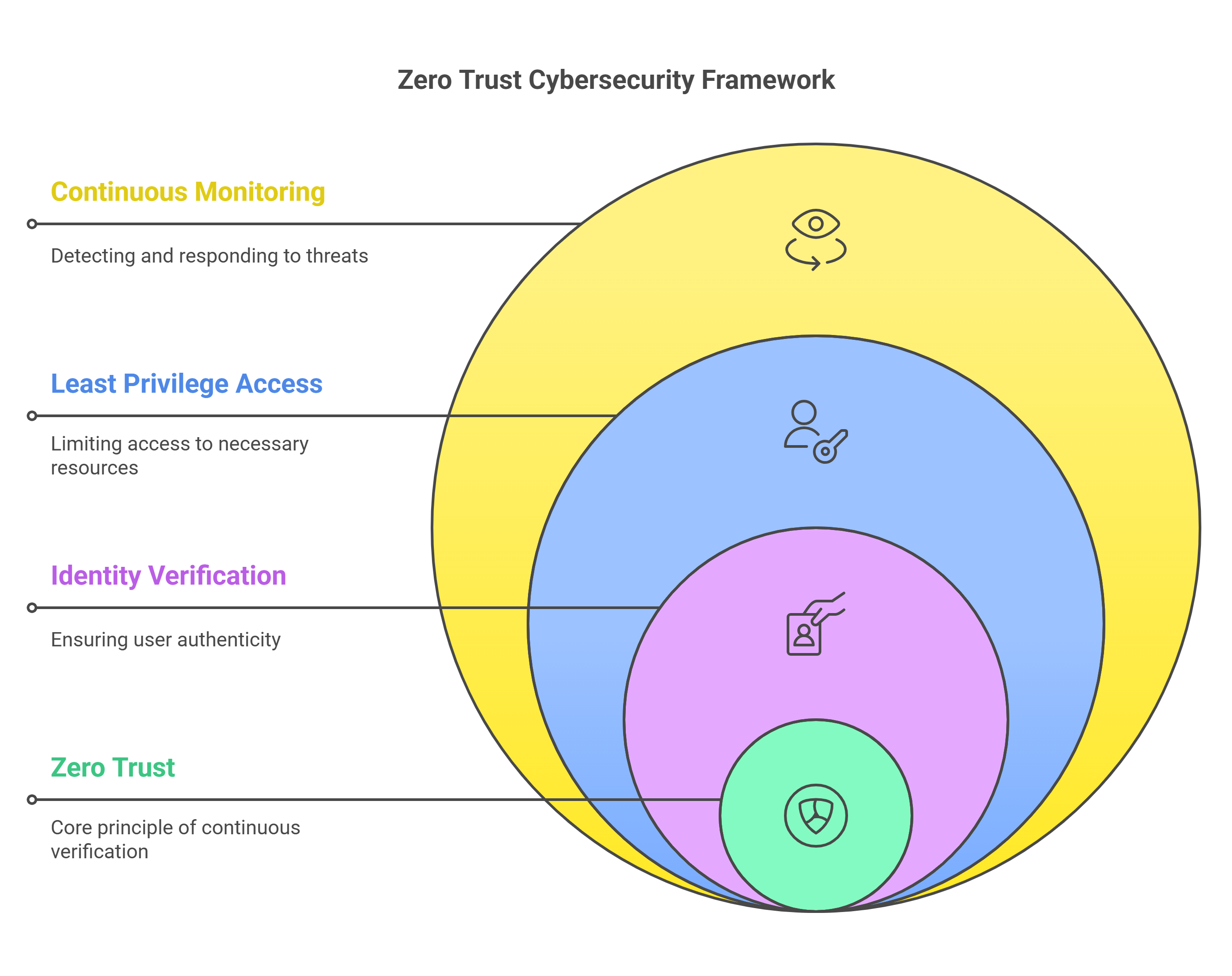
Zero Trust: The "Suspicious Butler" of Cybersecurity
Think of your network like a fancy mansion, and Zero Trust is your incredibly suspicious but highly effective butler. This butler doesn't care if you're the homeowner, a visiting dignitary, or the pizza delivery guy – everyone gets scrutinized before they can access anything.
-
"Who are you?" (Identity Verification): The butler (Zero Trust) wants to know exactly who is trying to access something. This means strong authentication like multi-factor authentication (MFA) – you know, that annoying but life-saving code you get on your phone after entering your password. It's like the butler asking for your ID and your secret handshake.
-
"What do you want?" (Least Privilege Access): Even if the butler knows who you are, they only grant you access to the specific rooms and items you need for your current task. The gardener doesn't get access to the vault, and the chef doesn't need the blueprints of the secret underground tunnel (unless it leads to a better spice rack, maybe?). In the digital world, this means users only get the permissions they absolutely need to do their job, minimizing the damage if their account is compromised.
"Are you behaving suspiciously?" (Continuous Monitoring): The butler is always on the lookout for anything out of the ordinary. If the homeowner suddenly starts trying to access the basement at 3 AM wearing a ski mask, the butler is going to raise an eyebrow (and probably call security). Similarly, Zero Trust constantly monitors user behavior and network traffic for any signs of malicious activity.
Zero Trust in Our Wild Work-From-Anywhere Reality
Now, let's see how our suspicious butler helps us in this modern hybrid work jungle:
-
The Coffee Shop Conundrum: You're working from your favorite coffee shop, connected to public Wi-Fi (gasp!). In the old "castle" model, once your device connected via VPN, it was somewhat trusted. But with Zero Trust, even though you're on that potentially risky network, every time your device or user tries to access a sensitive company file or application, it's re-verified. MFA kicks in, device health is checked, ensuring only authorized and healthy devices get access. It's like the butler checking your credentials every single time you try to open a different cabinet in the coffee shop.
-
The Personal Device Dilemma: Your CEO wants to quickly check some sales figures on their personal tablet while waiting for their flight. Traditional security might struggle with this "unmanaged" device. Zero Trust doesn't care what device it is. It focuses on the user's identity, the device's security posture, and the specific resource being requested. So, even on a personal tablet, the CEO would need to authenticate strongly, and the device might need to meet certain security standards before accessing sensitive data. The butler makes sure even the CEO's personal belongings are thoroughly vetted before entering the important rooms.
The Cloud Commotion: We're all living in the cloud now, with data and applications scattered across various services. Zero Trust provides a consistent security framework across this distributed environment. It's like having our suspicious butler stationed at the entrance of every room in our sprawling cloud mansion, regardless of who owns the room.
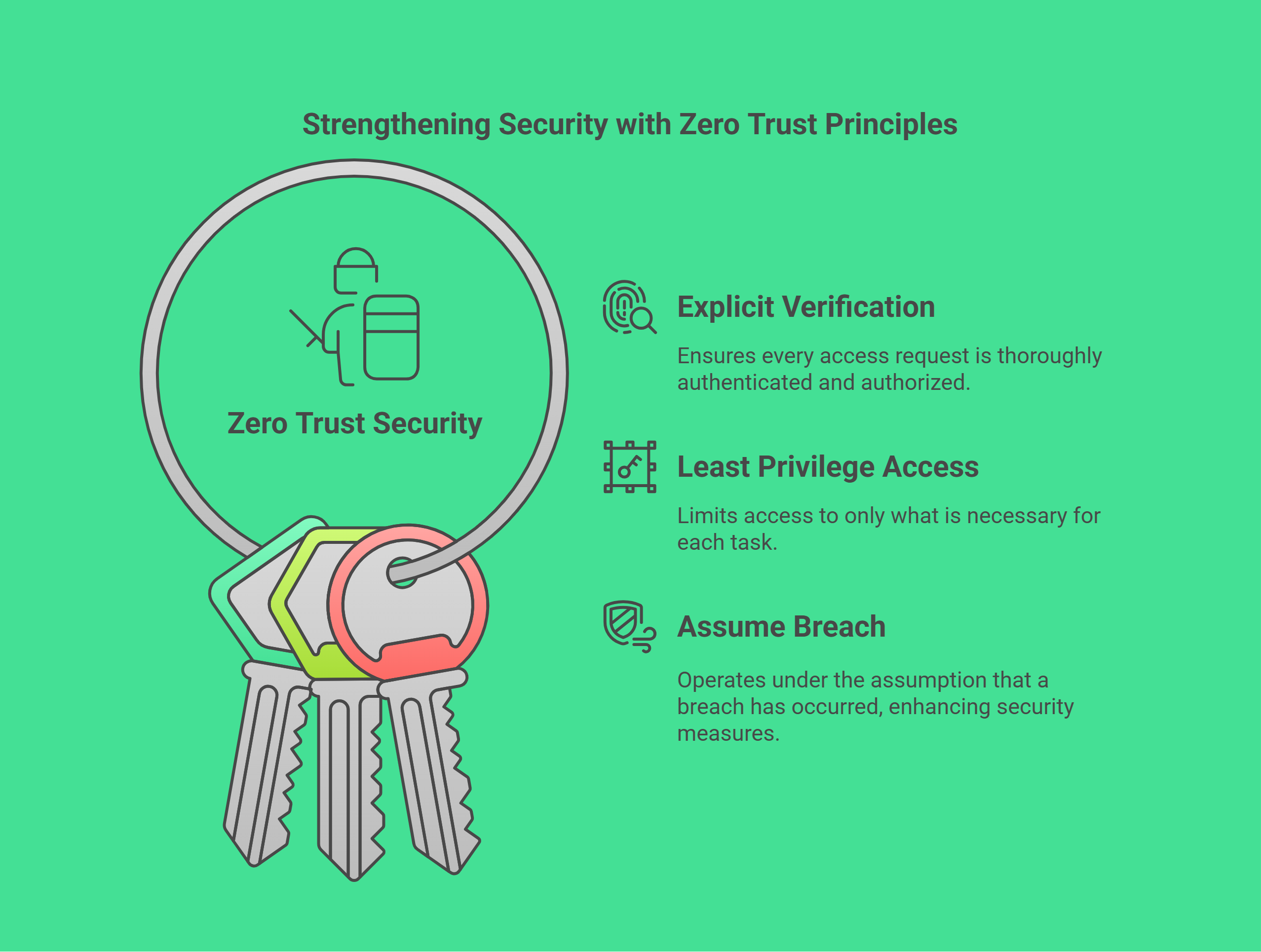
Key Principles of Zero Trust
Think of these as the butler's core rules:
Verify Explicitly: Always authenticate and authorize based on all available data points (user identity, device health, location, service, etc.).
Use Least Privilege Access: Grant only the minimum access needed to complete a task.
Assume Breach: Operate as if an attacker has already gained access and implement controls to limit their movement and potential damage (this is where continuous monitoring and segmentation come in).
TL;DR: Zero Trust in a Nutshell (or a Butler's Pantry)
Forget the "trust everyone inside" mentality. Zero Trust is all about "never trust, always verify," like a super suspicious but effective butler guarding your digital mansion. It uses strong identity verification (like MFA), grants only necessary access (least privilege), and constantly watches for suspicious activity. This is crucial in our work-from-anywhere world where devices and networks are diverse and potentially risky.
Ready to dive deeper into IT Security? Stay tuned for our next article.
 Add Row
Add Row  Add
Add 




Write A Comment