
The Digital Lock & Key Party: Key Exchange and Encryption Technologies Explained – CompTIA Security+ SY0-701 – 1.4 🔐
TL;DR 👀
Key exchange = securely trading secrets like it’s high school gossip, but encrypted.
Asymmetric encryption (public/private key pair) can safely generate a shared symmetric key.
Encryption tech like HSMs, TPMs, and secure enclaves protect keys like a vault inside a vault.
It’s all about trust, math, and not letting cyber-burglars crash the party.
The "Hey, Can I Trust You With My Secret?" Moment 🔑
Before two computers whisper encrypted sweet nothings to each other, they need to agree on a shared secret: a symmetric key. But how do they exchange this key without shouting it across the internet where digital eavesdroppers are lurking?
Enter the Key Exchange process. This is where asymmetric encryption saves the day (and your data).
Public + Private = 💘 Symmetric?
Yup, asymmetric encryption uses two keys:
A public key (share this with the world)
A private key (hide this like it’s your browser history)
When Alice wants to send Bob a secret symmetric key, she encrypts it using Bob’s public key. Only Bob can decrypt it with his private key. Once Bob has the symmetric key, they can both start talking fast and securely using symmetric encryption.
Why not just use asymmetric encryption the whole time? Because it’s slow. Like, “dial-up internet trying to stream Netflix” slow. Symmetric encryption is much faster once the secure tunnel is set.
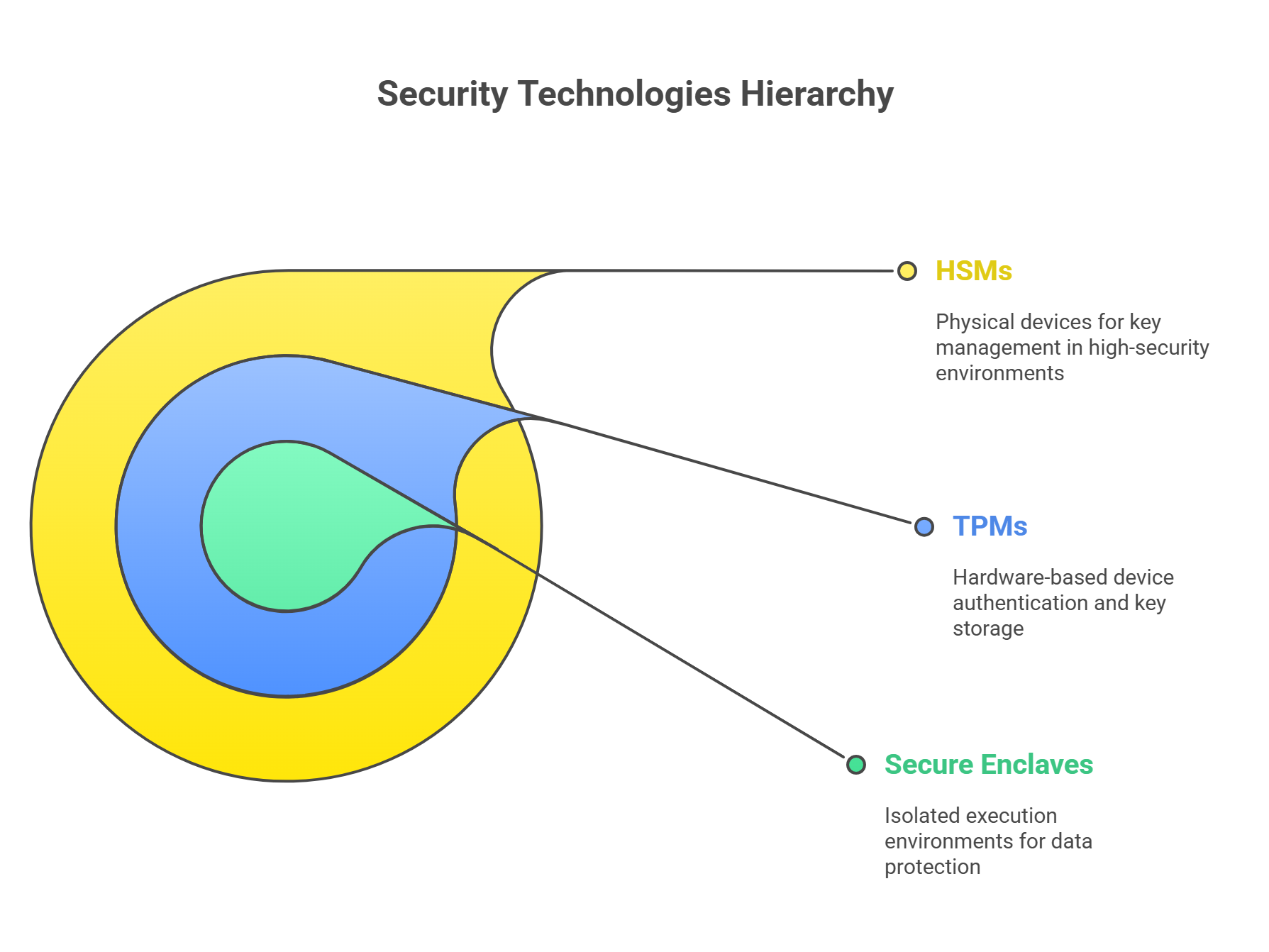
HSMs, TPMs, and Secure Enclaves: The Bodyguards of Your Encryption Squad 🛡️
💾 HSM (Hardware Security Module)
Think of it as the Fort Knox for encryption keys. HSMs are physical devices (usually in datacenters) designed to generate, store, and manage encryption keys in an environment that’s harder to break into than your ex’s emotional boundaries.
Expert Source: According to NIST SP 800-57, HSMs should be used in high-security environments for key lifecycle management.
🧠 TPM (Trusted Platform Module)
TPMs are like having a mini-HSM soldered directly onto your motherboard. They’re mostly used for:
Device authentication
BitLocker encryption
Storing keys securely even if the OS gets compromised
Microsoft’s own documentation calls TPM “a root of trust for reporting platform integrity.”
Basically: if you don’t have TPM 2.0, Windows 11 might ghost you.
🧬 Secure Enclaves
Secure enclaves (like Intel SGX) are isolated execution environments within a CPU. Code and data inside them can’t be seen or tampered with—even by malware with admin rights. It’s like having a private VIP room inside your processor where the secrets chill.
Encryption Tech in Real Life 🔒
Database Encryption: Keep stored data locked up like a paranoid dragon hoarding gold. Tools like TDE (Transparent Data Encryption) encrypt database files directly.
Transport Encryption: Protects data in motion (e.g., HTTPS, SSL/TLS) – because sending unencrypted data across the internet is like mailing a love letter on a postcard.
Key Management Systems (KMS): Centralized platforms to rotate, archive, and retire keys like an HR department for your encryption workforce.
Quoting the Pros 🧠
-
Bruce Schneier, cybersecurity legend, says:
“Encryption works. Properly implemented strong crypto systems are one of the few things that you can rely on.”
(Source: Schneier on Security blog) -
Dr. Eric Cole, author of Cybersecurity for Dummies, notes:
“The strength of encryption lies not only in the algorithm but in the protection and management of the keys.”
Translation: You can have the best locks in the world—but if your key’s taped to the door, you’re toast. 🔥
TL;DR Again (For the Scrollers in the Back) 🌀
Key exchange = passing the secret note (symmetric key) safely using asymmetric encryption
Encryption tech = secure lockers (TPMs, HSMs, enclaves) that hold your digital treasure
Without secure key handling, your encryption is basically a padlock made of cardboard
Final Thoughts: If You Liked This, You’ll Love What’s Next 🚀
Key exchange and encryption tech are the secret sauce to cybersecurity’s spicy recipe. But they’re just one dish in the buffet that is Security+ SY0-701.
👉 Dive into more tasty, brain-boosting articles and videos on our site. Your future as a cyber guardian depends on it.
Because in a world full of cyber villains… you don’t just need keys.
You need the right ones—and a fortress to keep them in.
Security+, encryption, key exchange, HSM, TPM, symmetric keys, asymmetric keys, secure enclave, cybersecurity fundamentals, SY0-701, IT certification
 Add Row
Add Row  Add
Add 




Write A Comment