
Security Reports That Don’t Suck: How to Make the Boss Actually Care
Why Most Security Reports Are Sleep Aids 😴
Let’s be real—most security reports look like they were written by a sleep-deprived robot trying to win a Pulitzer in Bureaucratic Nonsense. Pages of logs, 12-point Times New Roman, zero visuals… and a conclusion that basically says, “Threats are bad.” Riveting. 🙄
And then we wonder why leadership doesn’t take security seriously.
Rule #1: Know Your Audience (Hint: It’s Not Your Firewall)
Your C-suite isn’t looking for packet captures or port numbers. They want answers to these questions:
Are we safe?
What’s the risk?
How much is this going to cost us?
Who do we blame?
Translation: Your report needs to turn cybersecurity jargon into something even your CEO’s golden retriever could understand.
The Anatomy of a Security Report That Doesn’t Suck
🧠 1. Lead With the TL;DR
Give them the executive summary in two paragraphs. Highlight:
What happened
Why it matters
What you did
What’s next
If they only read this part (they will), make it count.
📸 2. Show, Don’t Just Tell
Graphs. Charts. Screenshots. Diagrams.
Would you rather read a 500-word explanation of traffic spikes or look at this?
Visuals take your report from “meh” to “oh snap” in seconds.
Bonus: Pie charts make even ransomware feel less scary. 🍰
⚖️ 3. Balance Technical Detail + Business Impact
Sure, you want to show off that deep dive into CVE-2023-Exploit-of-the-Week—but tie it to the bottom line. Like this:
Tech: RCE via unpatched web app
Business: If exploited, attackers could access customer PII, triggering compliance fines and legal risk
Now you’ve got their attention. And probably a budget increase.
😂 4. Humor Helps (When Used Wisely)
Don't be afraid to drop a little spice into your spice-less PDF.
Bad example:
“Incident X occurred at 4:32 PM”
Better:
“At 4:32 PM, someone clicked a sketchy link. Again. Karen, we need to talk.”
It makes your point and humanizes your message. Just don’t roast your team too hard. HR frowns on that. 👀
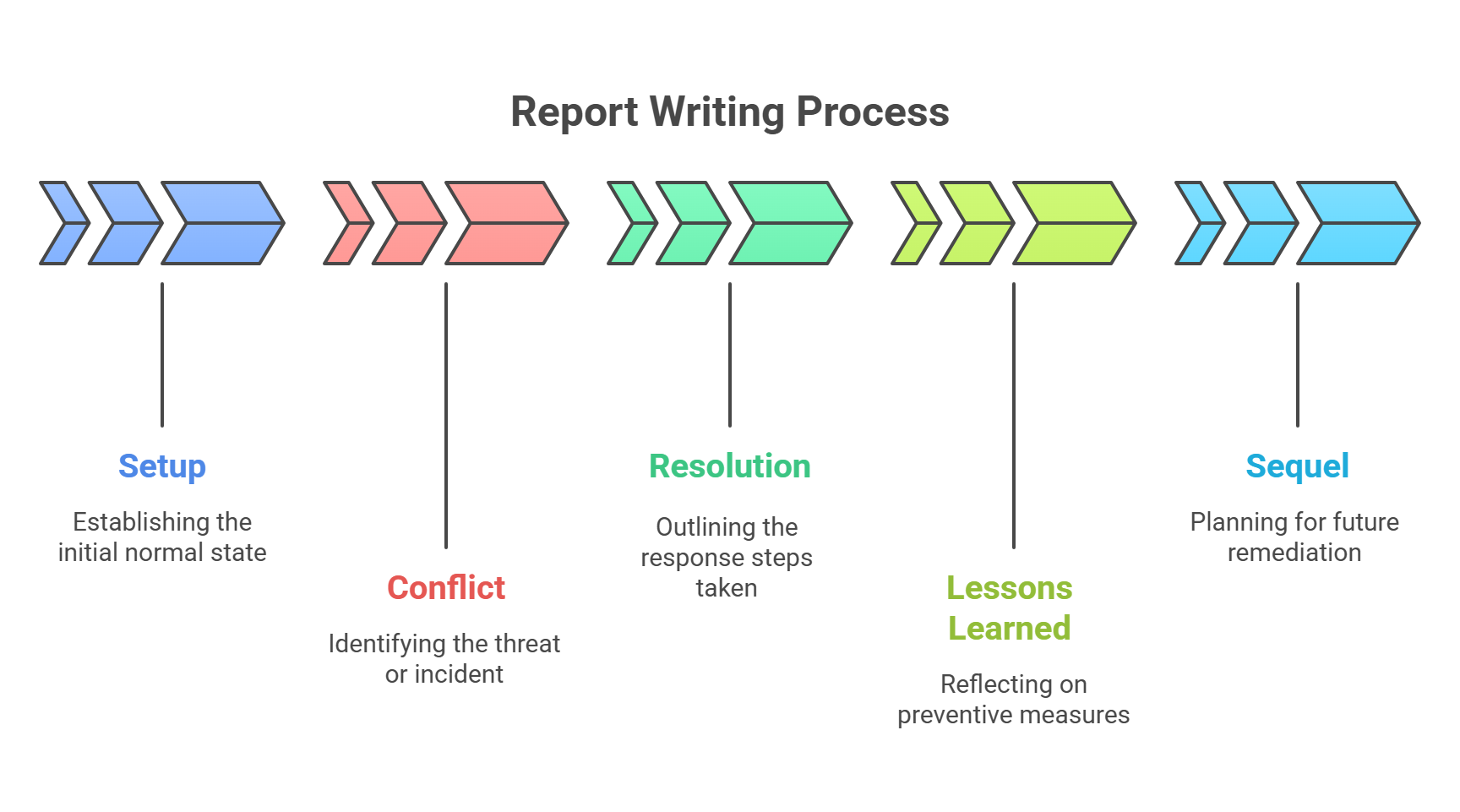
🪜 5. Tell a Story: Setup → Conflict → Resolution → Lessons
A good report reads like a good heist movie.
Setup: What normal looked like
Conflict: The threat or incident
Resolution: Your response steps
Lessons Learned: How it’s being prevented going forward
And yes, every good report has a sequel: the remediation plan. 🎬
🛠️ 6. Tools That Make Reporting Less Painful
MITRE ATT&CK Navigator – maps threats in human-readable form
Tableau / Power BI – data viz made pretty
Draw.io / Lucidchart – create awesome network diagrams
Canva – for when you want your report to look like a TED Talk slide deck
Because if it looks good, they’ll assume it must be smart too. 📊
The Report Hall of Shame 🧻
Some classics that deserve a roasting:
“This report details event ID 4625 repeated 934 times.” (Yawn.)
“See attached logs for more info.” (No one’s opening that ZIP file, Brad.)
“Threat actor activity noted.” (Wow, that’s super specific.)
Final Thoughts: Make Security Memorable
A great security report does three things:
Educates
Influences
Gets read
If your boss actually asks questions after reading it? You won. 🏆
If they laugh once? You’re a legend. 😎
And if they approve that new tool budget? You’re a cyber unicorn. 🦄
 Add Row
Add Row  Add
Add 




Write A Comment