
Secrets, Signatures & Sneaky Stuff: Digital Certificates, Hashing, Authentication & Obfuscation – CompTIA Security+ SY0-701 – 1.4 🕵️♂️
Explore hashing, digital certs, auth factors, and obfuscation like steganography in this fun, fast, Security+ SY0-701 deep dive. Learn the hidden tricks of cybersecurity in plain English.
TL;DR 👀
Digital certificates prove identity online—like digital driver’s licenses with encryption.
Hashing = irreversible data fingerprints. Great for checking integrity.
Authentication factors come in 3+ flavors: something you know, have, are, do, or where you are.
Obfuscation is the art of hiding things in plain sight (tokenization, steganography, data masking = the ultimate hide-and-seek champions).
Together, these build the backbone of secure communication and data protection in the modern world.
Digital Certificates: The Internet’s Secret Handshake 🤝
Imagine trying to buy something online and asking, “Are you really Amazon?”
Digital certificates are the receipts that say, “Yep, I’m legit. Verified by a trusted Certificate Authority (CA).”
They contain:
The public key of the entity
Info about the entity
A digital signature from the CA
Used in HTTPS, VPNs, and other encrypted sessions, they’re like security badges signed by the Internet’s most trusted gatekeepers.
“Digital certificates are the cornerstone of trust on the internet,” says David Bombal, cybersecurity educator and Cisco expert.
(Source: David Bombal’s YouTube Security+ series)
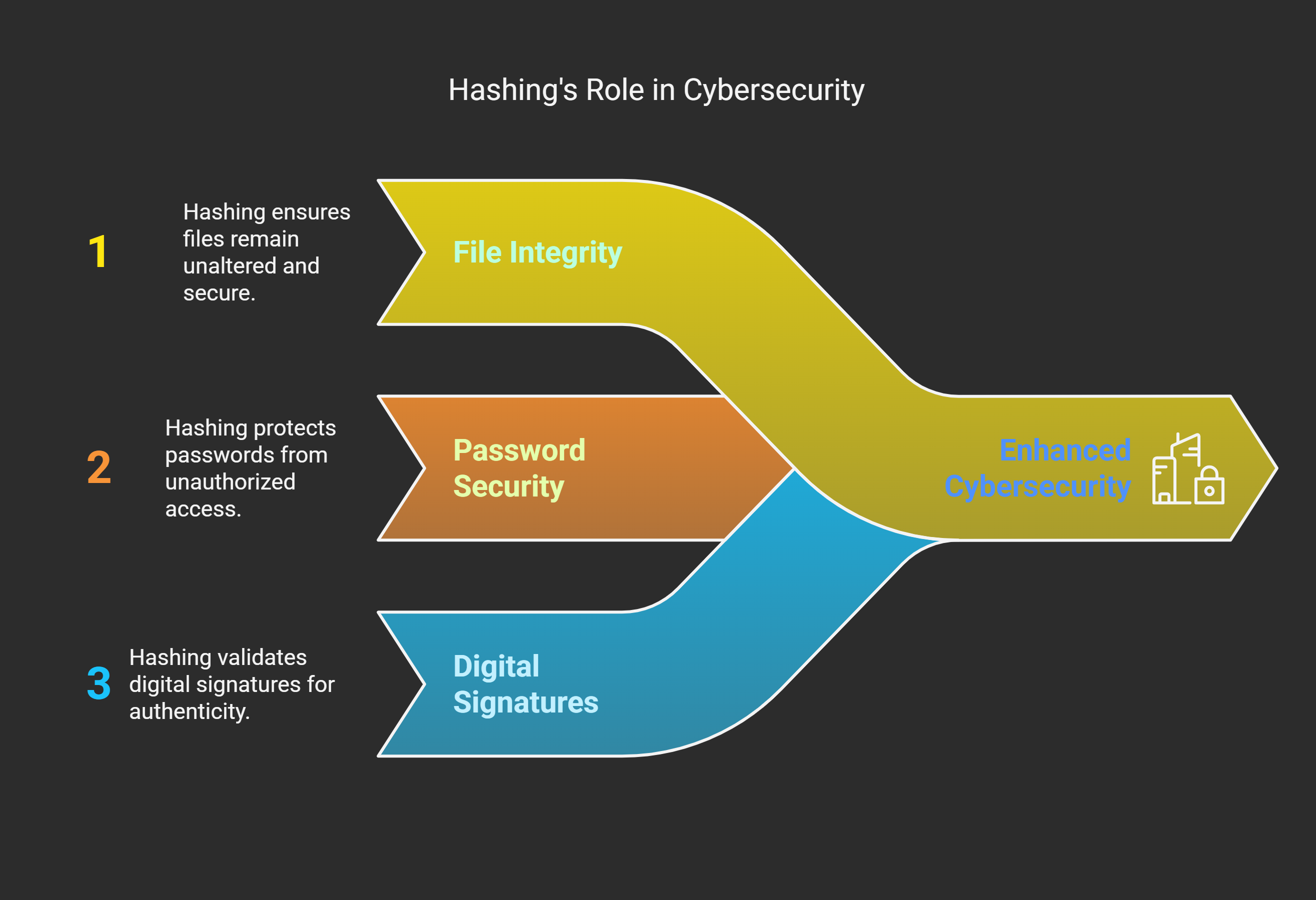
Hashing: The Tamper-Evident Seal of Cybersecurity 🧂
Think of hashing like seasoning your data with a secret spice mix that’s impossible to reverse-engineer.
It's used to:
Verify file integrity
Secure passwords
Validate digital signatures
Popular algorithms:
SHA-256 (used in everything from blockchain to SSL)
MD5 (still around, but cryptographically dead inside 😵)
🔑 Key fact: Hashing is not encryption. It’s a one-way function. You can’t unscramble a hash any more than you can un-toast toast.
Authentication Factors: Proving You’re Actually You 🙋♀️
Multifactor Authentication (MFA) is like being in a club where the bouncer asks for your ID, your mom’s maiden name, and the name of your first pet. Annoying? Maybe. Effective? Absolutely.
The 5 Authentication Factors:
Something you know – Passwords, PINs (easy to forget, easy to guess if it’s “123456”)
Something you have – Security token, smartphone, keycard
Something you are – Biometrics like fingerprint, face, or retinal scans
Something you do – Typing speed, mouse movement (yep, that’s a thing)
Somewhere you are – Geolocation, IP address-based checking
Combine two or more and you're making a hacker’s life way harder. Which is kinda the point. 😎
Obfuscation: Cybersecurity's Version of Misdirection 🎩✨
Obfuscation isn’t about making data secure—it’s about making it harder to understand or even detect. Like hiding broccoli in pizza so your kid won’t know they’re eating vegetables. 🍕
🖼️ Steganography
Hiding data in plain sight—like embedding a message in an image or audio file.
Digital spies use it. So do attackers. Also... digital artists, because why not?
Edward Snowden once said, “Encryption is the defense, but steganography is the camouflage.”
(Source: Glenn Greenwald, No Place to Hide)
🔁 Tokenization
Replacing sensitive data with a stand-in, like swapping a Social Security Number with a random ID token.
Used in payment systems, healthcare, and anywhere PII needs to be handled like radioactive material.
Real-world analogy:
You give a valet a token, not your car keys. Same idea.
🧼 Data Masking
Obscures sensitive data—think “XXXX-XXXX-1234” for credit cards.
The original data is still there under the hood, but it’s sanitized for testing, demos, or nosy coworkers.
It’s like sending a censored screenshot of a text thread. The juicy stuff’s still there—just not for everyone to see.
TL;DR Again for the TikTok Attention Spans 🌀
Digital certificates = ID cards for websites
Hashing = unique, irreversible fingerprints
Authentication factors = layered protection from bad guys and bots
Obfuscation = clever ways to hide your digital secrets
These concepts work together to keep the digital world running without becoming a hacker's playground.
Final Thoughts: You Now Know More Than 95% of the Internet 🔓
We just decoded some of the trickiest topics in Security+—without a PhD in cryptography or 15 cups of coffee. But trust me, there’s more awesome (and weirdly entertaining) stuff to learn.
👉 Check out the rest of our SY0-701 series to unlock more Security+ gold. The cert’s waiting, the job offers are lurking, and the memes write themselves.
Security+, digital certificates, hashing, authentication factors, steganography, tokenization, data masking, SY0-701, encryption, IT certification, cybersecurity
 Add Row
Add Row  Add
Add 




Write A Comment