
If Your Network Had a Therapist: Boundaries,
Policies & Keeping It Together
In reality, your network can be a hot mess sometimes. Devices bickering, bandwidth hogging, and the occasional full-blown meltdown (we call those outages). But what if I told you there's a way to bring peace and harmony to your digital domain? Enter: Network Policies. Think of them as the carefully crafted boundaries and expectations that prevent your network from going full reality TV.
Just like we need self-care to avoid burnout, our networks need policies to prevent digital drama. These aren't just stuffy rules; they're the foundation for a secure, efficient, and (dare I say) happy network.
What in the Digital World are Network Policies?
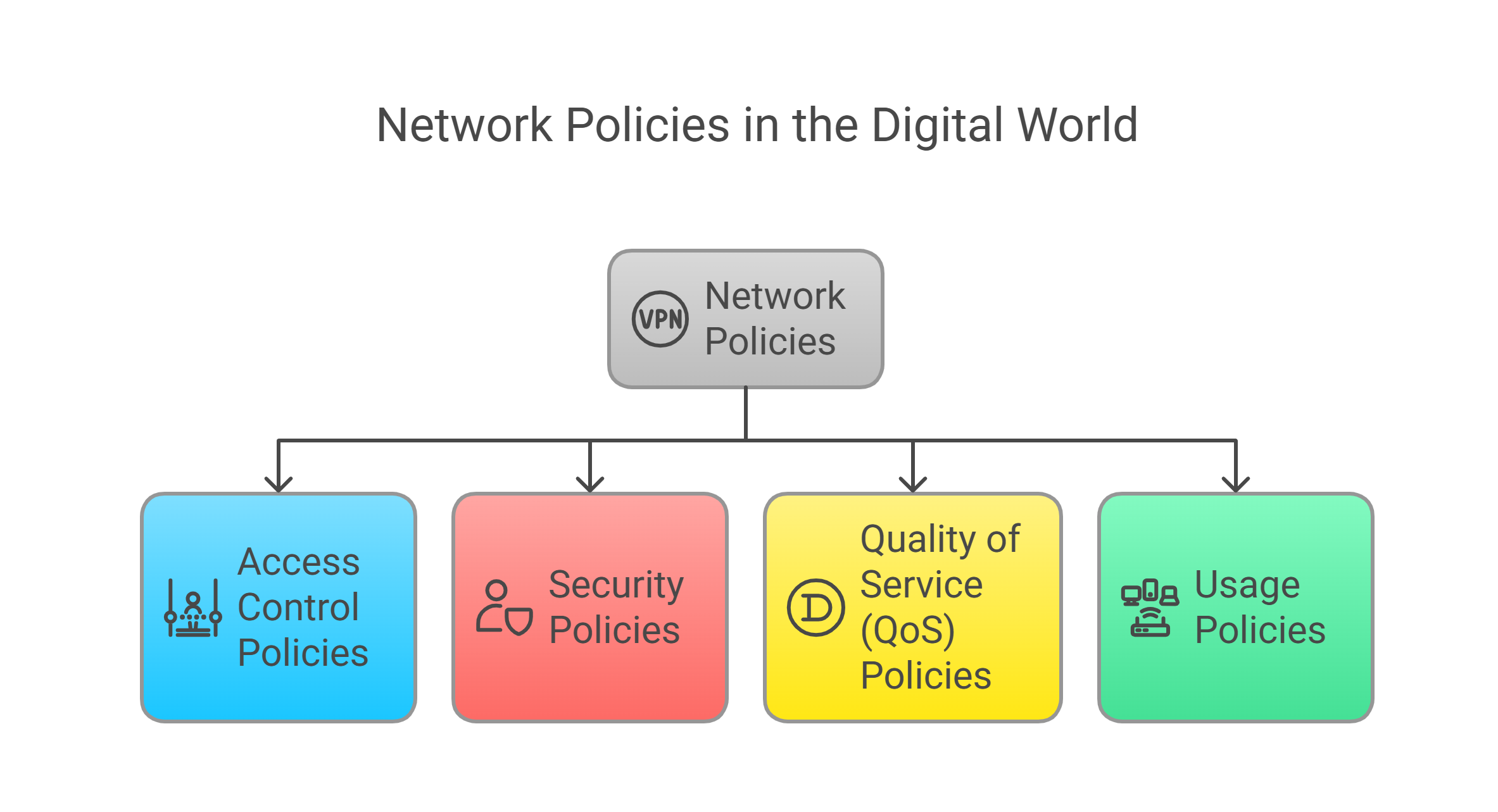
Imagine your network as a bustling city. Network policies are the traffic laws, zoning regulations, and even the neighborhood watch, all rolled into one. They are a set of rules that dictate how network resources are accessed, used, and protected. These policies can cover everything from who can access what data to how much bandwidth each application can consume.
Think of it this way:
Access Control Policies:
These are the bouncers at the digital nightclub, deciding who gets in and who doesn't. They ensure only authorized users and devices can access specific network resources. For example, the marketing team might have access to sales reports, but the HR department shouldn't (unless they're planning a surprise bonus!).
Security Policies:
These are the digital bodyguards, protecting your network from malicious attacks and unauthorized access. Think strong password requirements, firewall rules, and intrusion detection systems. As Bruce Schneier, a renowned security technologist, once wisely said, "Security is a process, not a product." These policies are the ongoing processes that keep the bad guys out.
Quality of Service (QoS) Policies:
These are the traffic cops, ensuring important data gets priority. Imagine a video conference call getting stuck behind a massive file download – QoS policies prevent this digital gridlock by prioritizing certain types of traffic.
Usage Policies:
These are the "house rules" for your network. They define acceptable and unacceptable uses of network resources, like internet browsing guidelines or restrictions on personal devices.
Best Practices: Keeping Your Digital House in Order
Now that we know what network policies are, let's talk about how to implement them like a seasoned pro. Here are some best practices to keep your network thriving:
Document Everything:
If it's not written down, it didn't happen (in the network world, anyway). Clearly document all your network policies, including who is responsible for enforcing them. Think of it as creating a network constitution – everyone needs to know the rules of the land.
Keep it Simple, Silly!
Overly complex policies are a recipe for confusion and errors. Aim for clarity and simplicity. Your policies should be easy to understand and implement. Don't make your network administrators feel like they're deciphering ancient hieroglyphics.
Regularly Review and Update:
The digital landscape is constantly evolving, so your policies shouldn't be set in stone. Regularly review and update them to reflect changes in your organization, technology, and security threats. Think of it as an annual network check-up – make sure everything is still healthy and relevant.
Communicate Clearly:
Make sure everyone who uses the network understands the policies. This includes employees, contractors, and even guests. Think of it as a friendly reminder before they connect – "Hey, just so you know, we have some rules to keep things running smoothly for everyone."
Enforce Consistently:
Policies are only effective if they are consistently enforced. No exceptions! Otherwise, it's like saying there's a speed limit, but winking at everyone who goes over.
Implement with Technology:
Leverage network management tools and technologies to automate policy enforcement. This reduces the risk of human error and ensures consistent application. Firewalls, intrusion prevention systems, and access control lists are your digital policy enforcers.
Train Your Users:
Educate your users on network policies and security best practices. Phishing scams and weak passwords are often the biggest vulnerabilities. As Kevin Mitnick, a famous former hacker (pictured below), once said,
"The human element is always the weakest link."
Training can help strengthen that link.

Best IT Certifications to Consider (If You're Digging This!)
So, you're finding this network policy stuff fascinating? Maybe it's time to level up your IT skills! Here are some top-notch certifications that can help you become a network policy ninja:
CompTIA Network+:
A foundational certification that covers essential networking concepts, including security and policies. It's like getting your network driver's license.
Cisco Certified Network Associate (CCNA):
A widely recognized certification focusing on Cisco networking technologies, including implementation and management of security and access control policies. Think of it as specializing in a popular brand of network vehicles.
Certified Information Systems Security Professional (CISSP):
A globally recognized certification for security professionals, covering a broad range of security topics, including policy development and implementation. This is like becoming a network security grandmaster.
Juniper Networks Certified Specialist (JNCIS):
If you're into Juniper Networks gear, this certification validates your skills in their networking and security technologies. It's like being a specialist in a different brand of high-performance network machines.
Wrapping It Up (Like a Securely Encrypted Package)
Network policies might not sound like the most thrilling topic, but they are the unsung heroes of a stable and secure IT infrastructure. By setting clear boundaries, establishing expectations, and consistently enforcing the rules, you can prevent digital chaos and keep your network running like a well-oiled (and well-therapized) machine. So go forth, implement these best practices, and give your network the self-care it deserves!
 Add Row
Add Row  Add
Add 




Write A Comment